09/04/2018
11/01/2018
27/11/2017
10/10/2017
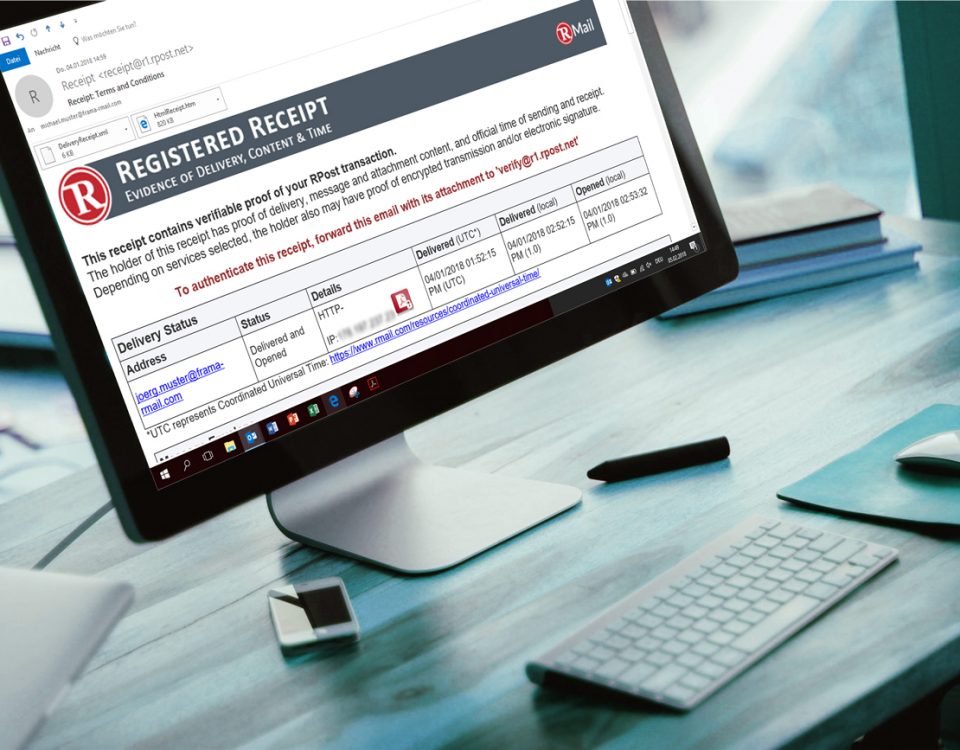
Part 3 of our series: “Done any tricks today?“ addresses solutions for ensuring verifiable and secure e-mail correspondence. In addition, we should not forget the EU […]
19/07/2017
When it comes to the delivery of standard e-mails, employees have little faith in the technology. How often is the phone grabbed simply to ask “has […]
13/06/2017
In this series, which will be published at irregular intervals, we will take a closer look at the subject of “e-mails”, in particular which effects the […]
24/05/2017
14/03/2017
This template supports the sidebar's widgets. Add one or use Full Width layout.