Done any tricks today? About Email missunderstandings and half-truths (part 2)
Done any tricks today? About Email missunderstandings and half-truths (part 1)
13/06/2017Striking a balance between cost and benefit for e-mail encryption (Part 1)
27/07/2017In part 1 we discussed the topic of blind trust with standard e-mails and the possibilities of altering their contents without leaving a trace. In other words, trust is good, but control is definitely better in this case.
Did my email arrive?
When it comes to the delivery of standard e-mails, employees have little faith in the technology. How often is the phone grabbed simply to ask "has my e-mail arrived?". And for good reason, because even if no error message is received, the e-mail may still not have been delivered. Some e-mail servers simply remain “mute”. But why is this? Because spammers often try to collect valid e-mail addresses. They attempt to send to y.name@yourfirm.com, your.name@yourfirm.com, your.n@yourfirm.com, and so on. Since most of these addresses do not exist, e-mail servers would send thousands of error messages and could themselves be classified as spammers.
In short, there is no guarantee that any e-mail will actually be delivered!

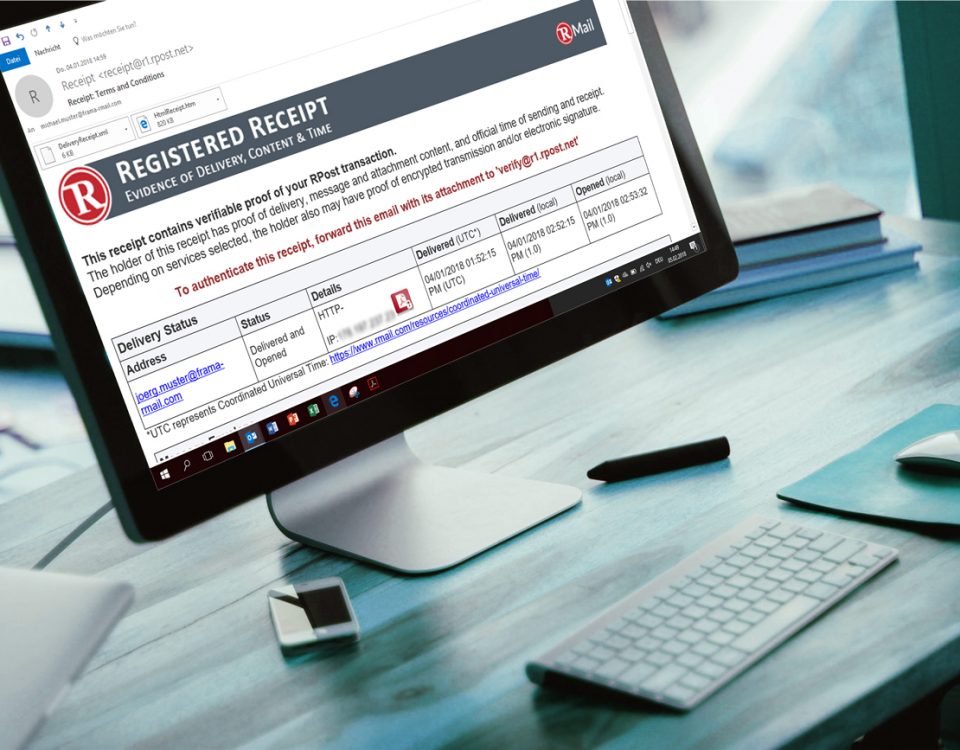
Read receipts...
Unfortunately, read receipts typically do not include information about the original content of the message that was opened for reading, and the e-mails saved under “Sent Items” have no value (see part 1). To take this a step further, many users don't allow the sending of read receipts (including the author of this article) because they are annoying.
In short, there is no guaranteed way to know who has opened what and when.
How then can e-mail communications be made verifiable, comprehensible, compliance with data protection and auditable?

This is hardly possible with the available means, since in order to design all traffic in a verifiable, comprehensible and auditable manner, it must be possible to answer the following question without any doubt:
who sent what, when and to whom? Let's break this down into its component parts:
- Who / whom: this relates to the topic of sender and receiver authentication, or detailed information about the sending and receiving process.
- When: Desktop times can be easily manipulated. For the determination of the time, it must be possible to refer to the standard time. For example, the UTC time would be a good option here.
- What: in order to verify the sent content without any doubt, it must be possible to reconstruct the original document in terms of the form and format in a tamper-proof manner.
- How: in order to prove how an (encrypted, unencrypted) e-mail was transmitted, it must be possible to prove that the e-mail has reached the recipient in encrypted or unencrypted form.
So there are a number of issues that need to be considered and resolved. We will investigate one possible approach in part 3 of this series.